Checkpoints
Update DEFINER clauses to INVOKER on the MySQL source instance.
/ 10
Create and save a Database Migration Service job without starting the job.
/ 20
Create users on the Cloud SQL destination instance.
/ 10
Start a previously created Database Migration Service job.
/ 10
Confirm the user metadata in Cloud SQL for MySQL
/ 10
Migrating MySQL User Data When Running Database Migration Service Jobs
- GSP861
- Overview
- Objectives
- Setup
- Task 1. Identify the existing MySQL users on the source instance
- Task 2. Update DEFINER to INVOKER on the MySQL source instance
- Task 3. Create and save a Database Migration Service job without starting it
- Task 4. Create the necessary users on the Cloud SQL destination instance
- Task 5. Run a previously created migration job
- Task 6. Confirm the user metadata in Cloud SQL for MySQL
- End your lab
GSP861
Overview
Database Migration Service provides a high-fidelity way to migrate MySQL database objects (including schema, data, and metadata) from a source database instance to a destination database instance. When you run a Database Migration Service job, all tables from all databases and schemas are migrated, with the exception of the following system databases: sys, mysql, performance_schema, and information_schema.
MySQL system databases, which are not migrated during Database Migration Service jobs, contain information about users and privileges (additional details available in the Migration fidelity Guide). You can manage users and privileges in the destination Cloud SQL database instance after it is created.
Objects that contain metadata defined with the DEFINER clause can fail when invoked on the destination instance, if the user associated with the DEFINER clause does not already exist in the destination instance (additional details available in the Create and run a MySQL migration job containing metadata with a DEFINER clause Guide).
To prevent errors when these objects are invoked on the destination instance after migration, you can complete one of the following actions before running the migration job:
- Create the necessary users on the MySQL destination instance, so that all users associated with DEFINER clauses are present in the destination instance; OR:
- Update DEFINER clauses to INVOKER on the MySQL source instance. This ensures that the security privileges used to access the data on the destination instance are set to the privileges for the user running the query, rather than the privileges for the user who defined the object.
In this lab, you learn how to ensure that your Cloud SQL for MySQL instance contains the relevant user metadata that was available on the MySQL source instance by completing both of the identified actions before running the migration job. First, you identify the existing MySQL users on the source instance and update DEFINER clauses to INVOKER for database objects on the source instance. Next, you create and save a Database Migration Service job. Before running the migration job, you create the necessary users on the destination database instance. Finally, you start the saved migration job; after the job runs successfully, you check the user metadata in the Cloud SQL for MySQL instance.
Objectives
In this lab, you learn how to migrate MySQL user data when running Database Migration Service jobs.
- Identify existing MySQL users on the source instance.
- Update DEFINER clauses to INVOKER on the MySQL source instance.
- Create and save a Database Migration Service job without starting the job.
- Create users on the Cloud SQL destination instance.
- Start a previously created Database Migration Service job.
- Check user metadata in the Cloud SQL destination instance.
Setup
For each lab, you get a new Google Cloud project and set of resources for a fixed time at no cost.
-
Sign in to Qwiklabs using an incognito window.
-
Note the lab's access time (for example,
1:15:00), and make sure you can finish within that time.
There is no pause feature. You can restart if needed, but you have to start at the beginning. -
When ready, click Start lab.
-
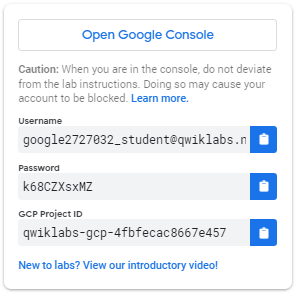
Note your lab credentials (Username and Password). You will use them to sign in to the Google Cloud Console.
-
Click Open Google Console.
-
Click Use another account and copy/paste credentials for this lab into the prompts.
If you use other credentials, you'll receive errors or incur charges. -
Accept the terms and skip the recovery resource page.
How to start your lab and sign in to the Console
-
Click the Start Lab button. If you need to pay for the lab, a pop-up opens for you to select your payment method. On the left is a panel populated with the temporary credentials that you must use for this lab.
-
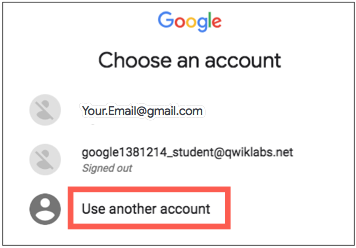
Copy the username, and then click Open Google Console. The lab spins up resources, and then opens another tab that shows the Choose an account page.
Note: Open the tabs in separate windows, side-by-side. -
On the Choose an account page, click Use Another Account. The Sign in page opens.
-
Paste the username that you copied from the Connection Details panel. Then copy and paste the password.
- Click through the subsequent pages:
- Accept the terms and conditions.
- Do not add recovery options or two-factor authentication (because this is a temporary account).
- Do not sign up for free trials.
After a few moments, the Cloud console opens in this tab.
Activate Google Cloud Shell
Google Cloud Shell is a virtual machine that is loaded with development tools. It offers a persistent 5GB home directory and runs on the Google Cloud.
Google Cloud Shell provides command-line access to your Google Cloud resources.
-
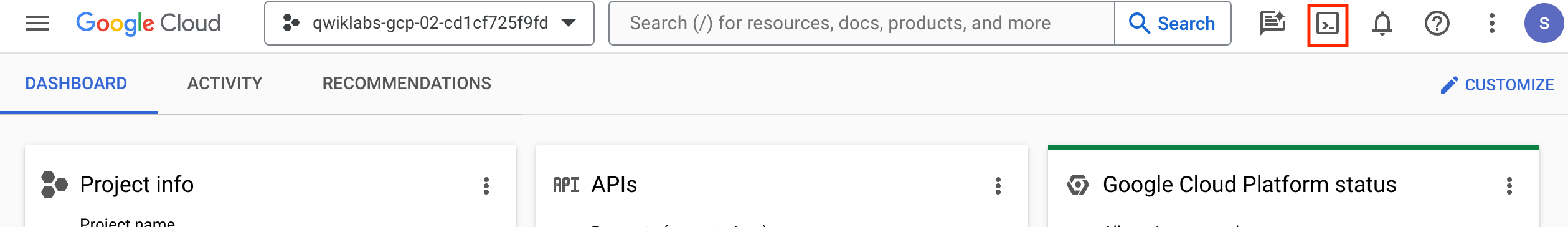
In Cloud console, on the top right toolbar, click the Open Cloud Shell button.
-
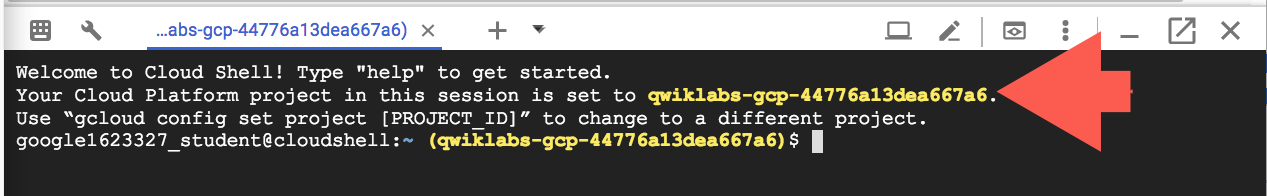
Click Continue.
It takes a few moments to provision and connect to the environment. When you are connected, you are already authenticated, and the project is set to your PROJECT_ID. For example:
gcloud is the command-line tool for Google Cloud. It comes pre-installed on Cloud Shell and supports tab-completion.
- You can list the active account name with this command:
Output:
Example output:
- You can list the project ID with this command:
Output:
Example output:
Verify that the Database Migration API is enabled
- In the Google Cloud Console, enter Database Migration API in the top search bar. Click on the result for Database Migration API.
This page either shows the status information, or gives you the option to enable the API.
- If necessary, enable the API.
Verify that the Service Networking API is enabled
- In the Google Cloud Console, enter Service Networking API in the top search bar. Click on the result for Service Networking API.
This page either shows the status information, or gives you the option to enable the API.
- If necessary, enable the API.
Task 1. Identify the existing MySQL users on the source instance
Similar to other Cloud resources, you can control Cloud SQL project access and permissions on the destination instance using Identity and Access Management (IAM) (details available in the IAM for Cloud SQL Guide).
In this task, you identify database users that are managed through database access control (read more in the About MySQL users Guide); for example, admins and superusers that can test the results of the migration job before others are provided access to the destination Cloud SQL instance via IAM.
Connect to the MySQL source instance
-
In the Google Cloud Console, on the Navigation menu (
), click Compute Engine > VM instances.
-
Locate the line with the instance called dms-mysql-training-vm.
-
For Connect, click on SSH to open a terminal window.
If prompted, click Authorize.
You can ignore any warnings about upgrades that appear in the SSH window.
- To connect to the MySQL interactive console within the terminal window, run the following command:
- When prompted for a password, enter:
Identify the existing MySQL users
- Run the following query to identify existing MySQL users:
Notice the system users named debian-sys-maint, mysql.session, and mysql.sys. These users do not need to be recreated, as they are created by MySQL as needed when the destination instance is created.
- Run the modified query to exclude these system users:
- Review the list of the users that need to be recreated in the destination Cloud SQL instance:
| host | user |
|---|---|
| localhost | admin |
| % | admin |
| localhost | bsmith |
| localhost | dwilliams |
| localhost | mhill |
| localhost | root |
| % | root |
In a later task, you create the root user when you run the Database Migration Service job. You also create the other users, after the Cloud SQL destination instance has been created by the migration job.
- Leave the terminal window open for use in the next task.
Task 2. Update DEFINER to INVOKER on the MySQL source instance
In the previous task, you identified the existing MySQL users on the source instance. In this task, you identify and update database objects that have DEFINER entries for either root or the other users that do not yet exist in the destination instance.
If you have not or will not create a user in the destination instance, then all DEFINER entries associated with that user need to be updated to INVOKER. Any DEFINER entries for root need to be updated to INVOKER using another user such as admin.
These actions prevent failures when the objects are invoked on the destination instance after migration (review additional documentation in the Create and run a MySQL migration job containing metadata with a DEFINER clause Guide).
Identify objects with DEFINER entries
To obtain information about DEFINERs in a MySQL instance, you can query the INFORMATION_SCHEMA tables to identify DEFINER entries that require review before migration (for example, DEFINER entries that are not associated with system databases such as mysql and thus will be migrated to the destination instance).
- Run the following query to identify DEFINER entries:
The results indicate that you need to check events, routines, triggers, and views for DEFINER entries.
Note that some of these DEFINER entries may be associated with system users, which do not require additional action. These system users are excluded in the queries to identify DEFINER entries for the various database objects.
- Run the following query to identify DEFINERs in events:
There are no instances of DEFINER in events associated with non-system users.
- Run the following query to identify DEFINERs in routines:
There are no instances of DEFINER in routines associated with non-system users.
- Run the following query to identify DEFINERs in triggers:
There are no instances of DEFINER in triggers associated with non-system users.
- Run the following query to identify DEFINERs in views:
- Review the details for the view named invoices_storenum_3656, which is associated with mhill:
| definer | security_type | table_schema | table_name |
|---|---|---|---|
| admin@localhost | DEFINER | customers_data | customers_single |
| admin@localhost | DEFINER | sales_data | invoices_storenum_5173 |
| bsmith@localhost | DEFINER | customers_data | customers_married |
| bsmith@localhost | DEFINER | sales_data | invoices_storenum_3980 |
| mhill@localhost | DEFINER | sales_data | invoices_storenum_3656 |
In the next section, you update DEFINER to INVOKER for this view.
Notice that one of the previously identified users (dwilliams) is not associated with any DEFINER entries in views. Additionally, notice that there are no instances of DEFINER for the root user. No action is needed for either dwilliams or root.
Update DEFINER to INVOKER
In this subtask, you update the DEFINER entries associated with mhill to INVOKER.
- Run the following command to see the details of the view associated with mhill:
- Select the database associated with the view:
- Run the following command to update DEFINER to INVOKER for the view:
- Review the DEFINER entries again to see that the view has been updated with INVOKER:
Notice that the DEFINER entry associated with mhill has been updated to INVOKER, while the DEFINER entries associated with admin and bsmith remain.
End the terminal session
- Exit the MySQL interactive console:
- Exit the terminal session:
Click Check my progress to verify the objective.
Task 3. Create and save a Database Migration Service job without starting it
In this task, you create and save a migration job without starting the job. Specifically, you create a one-time migration job using VPC peering as the connectivity option; however, you can create and save any migration job to run at a later time.
This allows you to create the destination Cloud SQL instance without migrating data until you have completed necessary tasks such as creating new users on the destination instance.
Get the connectivity information for the MySQL source instance
-
In the Google Cloud Console, on the Navigation menu (
), click Compute Engine > VM instances.
-
Locate the line with the instance called dms-mysql-training-vm.
-
Copy the value for Internal IP (e.g. 10.128.0.2).
Create a new connection profile for the MySQL source instance
-
In the Google Cloud Console, on the Navigation menu (
), click Database Migration > Connection profiles.
-
Click Create Profile.
-
For Database engine, select MySQL.
-
Enter the required information for a connection profile:
| Property | Value |
|---|---|
| Connection profile name | mysql-vm |
| Connection profile ID | keep the auto-generated value |
| Hostname or IP address | enter the internal IP for the MySQL source instance that you copied in the previous task (e.g. 10.128.0.2) |
| Port | 3306 |
| Username | admin |
| Password | changeme! |
| Region |
-
For the Encryption Type, select None.
-
Click Create.
A new connection profile named mysql-vm appears in the Connections profile list.
Create a new one-time migration job
-
In the Google Cloud Console, on the Navigation menu (
), click Database Migration > Migration jobs.
-
Click Create Migration Job.
-
For Create a migration job, on the Get Started tab, use the following values:
| Property | Value |
|---|---|
| Migration job name | vm-to-cloudsql |
| Migration job ID | keep the auto-generated value |
| Source database engine | MySQL |
| Destination region | |
| Migration job type | One-time |
Leave all other settings as default.
- Click Save & Continue.
Define the source instance
-
For source connection profile, select mysql-vm.
-
Leave the defaults for the other settings.
-
Click Save & Continue.
Create the destination instance
- Enter the required information to create the destination instance on Cloud SQL:
| Property | Value |
|---|---|
| Destination Instance ID | mysql-cloudsql |
| Root password | supersecret! |
| Choose a Cloud SQL edition | Enterprise |
| Database version | Cloud SQL for MySQL 5.7 |
| Zonal availability | Multiple zones (Highly available) |
-
For Instance connectivity, select Private IP and Public IP.
-
Select Use an automatically allocated IP range.
-
Click Allocate & Connect.
Note: This step may take a few minutes. If asked to retry the request, click the Retry button to refresh the Service Networking API.
When this step is complete, an updated message notifies you that the instance will use the existing managed service connection.- Enter the additional information needed to create the destination instance on Cloud SQL:
| Property | Value |
|---|---|
| Machine shapes | 2 vCPU, 8 GB |
| Storage type | SSD |
| Storage capacity | 10 |
- Click Create & Continue.
If prompted to confirm, click Create Destination & Continue.
Define the connectivity method
A message states that your destination database instance is being created. Continue to step 1 while you wait.
-
For Connectivity method, select VPC peering.
-
For VPC, select default.
VPC peering is configured by Database Migration Service using the information provided for the VPC network (the default network in this example).
- Wait for the Cloud SQL for MySQL instance to be created.
When you see an updated message that the destination instance was created, proceed to the next step.
- Click Configure & Continue.
Save the one-time migration job
-
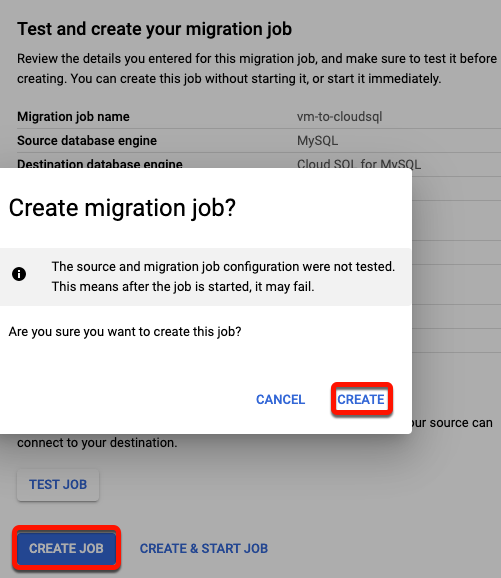
Review the details of the migration job.
-
Click Create Job.
You do not need to test the migration job. Recall that testing the job now will result in an error message because there are DEFINER entries associated with users that have not yet been created in the destination instance. You create these users in the next task.
- If prompted to confirm, click Create.
The migration job has been created but has not been started. You start the job in a later task, after you create the new users in the Cloud SQL destination instance.
Click Check my progress to verify the objective.
Task 4. Create the necessary users on the Cloud SQL destination instance
In Cloud SQL, you can create MySQL users, such as admins and superusers, who can test the results of the migration job before others are provided access via IAM. In addition, you want to create users that have DEFINER clauses associated with them, before you run a migration job.
In this task, you create the users named admin, bsmith, and mhill.
-
In the Google Cloud Console, on the Navigation menu (
), click SQL.
-
Expand the mysql-cloudsql-master instance and click on the instance ID called mysql-cloudsql.
-
In the Replica Instance menu, click Users.
-
Click Add User Account.
-
For User name, enter: admin
-
For Password, enter: changeme!
-
For Host name, select Restrict host by IP address or address range.
-
For Host, enter: localhost
-
Click Add.
-
Repeat steps 4-9 to create two more users with localhost access:
| User | Password |
|---|---|
| bsmith | mustchangeasap! |
| mhill | update! |
Click Check my progress to verify the objective.
Task 5. Run a previously created migration job
Start a migration job
-
In the Google Cloud Console, on the Navigation menu (
), click Database Migration > Migration jobs.
-
Click the migration job vm-to-cloudsql to see the details page.
-
Click the Start button to run the migration job.
If prompted to confirm, click Start.
- Review the migration job status.
- If you have not started the job, the status is Not started. You can choose to start or delete the job.
- After the job has started, the status is Starting and then transitions to Running.
- When the job status changes to Completed, the migration job has completed successfully, and you can move on to the next task.
Click Check my progress to verify the objective.
Task 6. Confirm the user metadata in Cloud SQL for MySQL
Connect to the MySQL instance
-
In the Google Cloud Console, on the Navigation menu (
), click SQL.
-
Click on the instance ID called mysql-cloudsql.
-
In the Primary Instance menu, click Overview.
-
In Connect to this instance panel, click Open Cloud Shell.
The command to connect to MySQL will pre-populate in Cloud Shell:
- Run the pre-populated command.
If prompted, click Authorize for the API.
- When prompted for a password, which you previously set, enter:
You have now activated the MySQL interactive console.
Review the user metadata in the Cloud SQL for MySQL instance
- Run the following query to see non-system users:
Notice the users that you created in the previous task.
- Run the following query to see that the user metadata has been migrated successfully:
- Review the entries to see that the metadata for invoices_storenum_3656 was migrated successfully:
| definer | security_type | table_schema | table_name |
|---|---|---|---|
| admin@localhost | DEFINER | customers_data | customers_single |
| admin@localhost | DEFINER | sales_data | invoices_storenum_5173 |
| bsmith@localhost | DEFINER | customers_data | customers_married |
| bsmith@localhost | DEFINER | sales_data | invoices_storenum_3980 |
| mhill@localhost | INVOKER | sales_data | invoices_storenum_3656 |
- To select the database in the MySQL interactive console, run the following command:
- Query the view associated with mhill to check that it executes successfully:
- Exit the MySQL interactive console:
Click Check my progress to verify the objective.
End your lab
When you have completed your lab, click End Lab. Google Cloud Skills Boost removes the resources you’ve used and cleans the account for you.
You will be given an opportunity to rate the lab experience. Select the applicable number of stars, type a comment, and then click Submit.
The number of stars indicates the following:
- 1 star = Very dissatisfied
- 2 stars = Dissatisfied
- 3 stars = Neutral
- 4 stars = Satisfied
- 5 stars = Very satisfied
You can close the dialog box if you don't want to provide feedback.
For feedback, suggestions, or corrections, please use the Support tab.
Manual Last Updated October 17, 2023
Lab Last Tested October 17, 2023
Copyright 2022 Google LLC All rights reserved. Google and the Google logo are trademarks of Google LLC. All other company and product names may be trademarks of the respective companies with which they are associated.