Puntos de control
Use Terraform to set up the necessary infrastructure (Lab setup)
/ 50
Installing the hello server
/ 30
Deploy a second copy of the hello-clients app into the new namespace
/ 20
Cómo usar una política de red en Google Kubernetes Engine
- GSP480
- Descripción general
- Arquitectura
- Configuración y requisitos
- Tarea 1. Configuración del lab
- Tarea 2. Validación
- Tarea 3. Instala el servidor hello server
- Tarea 4. Confirma el acceso predeterminado a hello server
- Tarea 5. Restringe el acceso mediante una política de red
- Tarea 6. Restringe los espacios de nombres con políticas de red
- Tarea 7. Validación
- Tarea 8. Eliminación
- Tarea 9. Soluciona problemas en tu propio entorno
- ¡Felicitaciones!
GSP480
Descripción general
En este lab, aprenderás a aplicar restricciones precisas a la comunicación de red para mejorar la seguridad de tu instancia de Kubernetes Engine.
El Principio de mínimo privilegio es ampliamente reconocido como una importante consideración de diseño al momento de mejorar la protección de sistemas fundamentales contra las fallas y el comportamiento malicioso. Sugiere que cada componente pueda acceder solo a la información y los recursos necesarios para su propósito legítimo. Este documento demuestra cómo se puede implementar el principio de privilegio mínimo dentro de la capa de red de Kubernetes Engine.
Las conexiones de red se pueden restringir a dos niveles de tu infraestructura de Kubernetes Engine. El primer mecanismo, de menor precisión, es la aplicación de reglas de firewall a niveles de red, subred y host. Estas reglas se aplican fuera de Kubernetes Engine, a nivel de VPC.
Si bien las reglas de firewall son una medida de seguridad sólida, Kubernetes te permite definir reglas aún más precisas mediante las políticas de red. Las políticas de red se usan para limitar la comunicación dentro del clúster. No se aplican a los Pods conectados al espacio de nombres de red del host.
En este lab, aprovisionarás un clúster privado de Kubernetes Engine y un host de bastión mediante el cual accederás al clúster. Un host de bastión proporciona un solo host con acceso al clúster, el cual, al combinarse con una red privada de Kubernetes, garantiza que el clúster no esté expuesto a comportamientos maliciosos de Internet en general. Los hosts de bastión son particularmente útiles cuando no tienes acceso de VPN a la red de la nube.
Dentro del clúster, se aprovisionarán un servidor HTTP simple y dos Pods cliente. Aprenderás a usar una política de red y a establecer etiquetas para permitir solo las conexiones desde uno de los Pods cliente.
Los ingenieros de GKE Helmsman crearon este lab para ayudarte a comprender mejor la Autorización Binaria de GKE. Para ver esta demostración, ejecuta los comandos gsutil cp -r gs://spls/gke-binary-auth/* . y cd gke-binary-auth-demo en Cloud Shell. Te invitamos a hacer cualquier aporte que creas conveniente.
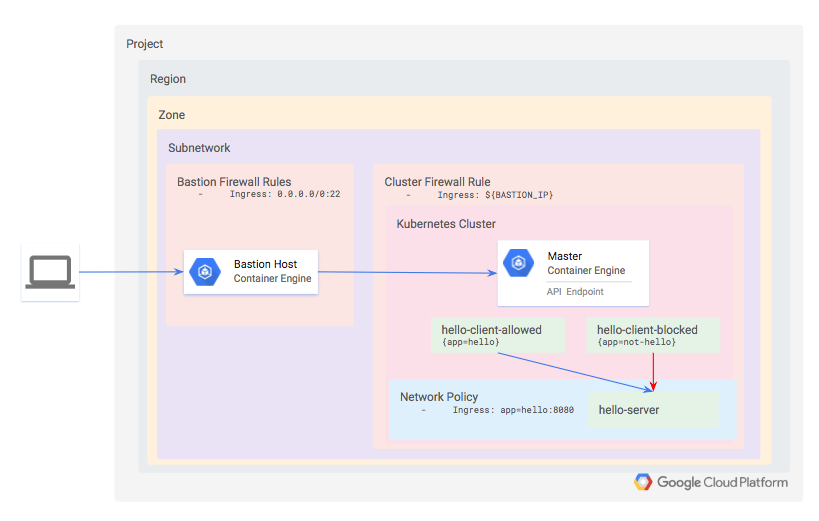
Arquitectura
Definirás un clúster privado de Kubernetes de modo estándar que use Dataplane V2. Dataplane V2 tiene políticas de red habilitadas de forma predeterminada.
Dado que el clúster es privado, no se podrá acceder a la API ni a los nodos trabajadores desde Internet. En su lugar, definirás un host de bastión y usarás una regla de firewall para habilitar el acceso al clúster. La dirección IP del host de bastión se define como una red autorizada para el clúster, la cual le otorga acceso a la API.
Dentro del clúster, aprovisiona tres cargas de trabajo:
- hello-server: Este es un servidor HTTP simple con un extremo accesible internamente.
- hello-client-allowed: Este es un Pod único que intenta de forma repetida acceder a hello-server. El Pod se etiquetará de tal manera que la política de red te permitirá conectarte a hello-server.
- hello-client-blocked: Este ejecuta el mismo código que hello-client-allowed, pero el Pod se etiquetará de tal manera que la política de red no le permitirá conectarse a hello-server.
Configuración y requisitos
Antes de hacer clic en el botón Comenzar lab
Lee estas instrucciones. Los labs son cronometrados y no se pueden pausar. El cronómetro, que comienza a funcionar cuando haces clic en Comenzar lab, indica por cuánto tiempo tendrás a tu disposición los recursos de Google Cloud.
Este lab práctico te permitirá realizar las actividades correspondientes en un entorno de nube real, no en uno de simulación o demostración. Para ello, se te proporcionan credenciales temporales nuevas que utilizarás para acceder a Google Cloud durante todo el lab.
Para completar este lab, necesitarás lo siguiente:
- Acceso a un navegador de Internet estándar (se recomienda el navegador Chrome)
- Tiempo para completar el lab: Recuerda que, una vez que comienzas un lab, no puedes pausarlo.
Cómo iniciar su lab y acceder a la consola de Google Cloud
-
Haga clic en el botón Comenzar lab. Si debe pagar por el lab, se abrirá una ventana emergente para que seleccione su forma de pago. A la izquierda, se encuentra el panel Detalles del lab que tiene estos elementos:
- El botón Abrir la consola de Google
- Tiempo restante
- Las credenciales temporales que debe usar para el lab
- Otra información para completar el lab, si es necesaria
-
Haga clic en Abrir la consola de Google. El lab inicia recursos y abre otra pestaña en la que se muestra la página de acceso.
Sugerencia: Ordene las pestañas en ventanas separadas, una junto a la otra.
Nota: Si ve el diálogo Elegir una cuenta, haga clic en Usar otra cuenta. -
Si es necesario, copie el nombre de usuario del panel Detalles del lab y péguelo en el cuadro de diálogo Acceder. Haga clic en Siguiente.
-
Copie la contraseña del panel Detalles del lab y péguela en el cuadro de diálogo de bienvenida. Haga clic en Siguiente.
Importante: Debe usar las credenciales del panel de la izquierda. No use sus credenciales de Google Cloud Skills Boost. Nota: Usar su propia Cuenta de Google podría generar cargos adicionales. -
Haga clic para avanzar por las páginas siguientes:
- Acepte los términos y condiciones.
- No agregue opciones de recuperación o autenticación de dos factores (esta es una cuenta temporal).
- No se registre para obtener pruebas gratuitas.
Después de un momento, se abrirá la consola de Cloud en esta pestaña.

Activa Cloud Shell
Cloud Shell es una máquina virtual que cuenta con herramientas para desarrolladores. Ofrece un directorio principal persistente de 5 GB y se ejecuta en Google Cloud. Cloud Shell proporciona acceso de línea de comandos a tus recursos de Google Cloud.
- Haz clic en Activar Cloud Shell
en la parte superior de la consola de Google Cloud.
Cuando te conectes, habrás completado la autenticación, y el proyecto estará configurado con tu PROJECT_ID. El resultado contiene una línea que declara el PROJECT_ID para esta sesión:
gcloud es la herramienta de línea de comandos de Google Cloud. Viene preinstalada en Cloud Shell y es compatible con la función de autocompletado con tabulador.
- Puedes solicitar el nombre de la cuenta activa con este comando (opcional):
-
Haz clic en Autorizar.
-
Ahora, el resultado debería verse de la siguiente manera:
Resultado:
- Puedes solicitar el ID del proyecto con este comando (opcional):
Resultado:
Resultado de ejemplo:
gcloud, consulta la guía con la descripción general de gcloud CLI en Google Cloud.
Clona la demostración
- Copia los recursos necesarios para este ejercicio de lab desde un bucket de Cloud Storage:
- Ve al directorio de la demostración:
- Haz que los archivos de demostración sean ejecutables con el siguiente comando:
Tarea 1. Configuración del lab
Primero, configura la región y la zona de Google Cloud.
- Configura la región de Google Cloud.
- Configura la zona de Google Cloud.
gcloud config set compute/zone "{{{project_0.default_zone|placeholder}}}"
En este lab, se usarán las siguientes APIs de servicio de Google Cloud, habilitadas para ti:
compute.googleapis.comcontainer.googleapis.comcloudbuild.googleapis.com
Además, la configuración de Terraform tiene tres parámetros para determinar dónde se debe crear el clúster de Kubernetes Engine:
project IDregionzone
Para mayor simplicidad, estos parámetros se especifican en un archivo llamado terraform.tfvars, en el directorio de terraform.
- Ejecuta el siguiente comando para asegurarte de que estén habilitadas las APIs adecuadas y generar el archivo
terraform/terraform.tfvarsbasado en tus valores predeterminados de gcloud:
- Escribe
ycuando se te pida confirmar.
Esto habilitará las API de servicio necesarias y también generará un archivo terraform/terraform.tfvars con las siguientes claves.
- Ejecuta el siguiente comando para verificar que los valores coincidan con el resultado de
gcloud config list:
Aprovisiona el clúster de Kubernetes Engine
- A continuación, aplica la configuración de Terraform en el directorio raíz del proyecto:
- Cuando se te solicite, revisa el plan generado e ingresa
yespara implementar el entorno.
La implementación tardará varios minutos.
Tarea 2. Validación
Terraform mostrará un mensaje cuando se haya creado el clúster de forma exitosa.
Prueba la tarea completada
Haz clic en Revisar mi progreso para verificar la tarea realizada. Si implementaste correctamente la infraestructura necesaria con Terraform, verás una puntuación de evaluación.
- Ahora, para los pasos restantes, establece una conexión SSH al host de bastión:
Las versiones existentes de kubectl y los clientes personalizados de Kubernetes contienen código específico del proveedor para administrar la autenticación entre el cliente y Google Kubernetes Engine. A partir de la versión 1.26, este código ya no se incluirá como parte del kubectl de OSS. Los usuarios de GKE deberán descargar y usar un complemento de autenticación independiente para generar tokens específicos de GKE. Este nuevo objeto binario, gke-gcloud-auth-plugin, usa el mecanismo complemento de credenciales Client-go de Kubernetes para extender la autenticación de kubectl y hacerla compatible con GKE. Para obtener más información, revisa la siguiente documentación.
Sigue estos pasos para que kubectl use el nuevo complemento de objeto binario para la autenticación, en lugar del código específico del proveedor.
- Luego de conectarte, ejecuta el siguiente comando para instalar
gke-gcloud-auth-pluginen la VM.
- Establece
export USE_GKE_GCLOUD_AUTH_PLUGIN=Trueen~/.bashrcde la siguiente forma:
- Ejecuta el siguiente comando:
- Ejecuta el siguiente comando para forzar la configuración de este clúster, de manera que se actualice a la configuración del complemento de credenciales Client-go.
Si la operación es exitosa, verás este mensaje:
El clúster recién creado estará disponible para los comandos estándar de kubectl en el host de bastión.
Tarea 3. Instala el servidor hello server
La aplicación de prueba consiste en un servidor HTTP simple, implementado como hello-server, y dos clientes, uno que se etiquetará como app=hello y el otro como app=not-hello.
Los tres servicios se pueden implementar al aplicar los manifiestos de hello-app.
- En el host de bastión, ejecuta el siguiente comando:
Resultado:
- Verifica que los tres Pods se hayan implementado correctamente:
Verás un Pod en funcionamiento por cada implementación de hello-client-allowed, hello-client-blocked y hello-server.
Prueba la tarea completada
Haz clic en Revisar mi progreso para verificar la tarea realizada. Si implementaste correctamente el servidor HTTP simple hello server, verás una puntuación de evaluación.
Tarea 4. Confirma el acceso predeterminado a hello server
- Primero, muestra las últimas líneas del cliente "permitido" con tail:
Para salir, presiona Ctrl+C.
- Segundo, muestra las últimas líneas de los registros del cliente "bloqueado":
- Para salir, presiona Ctrl+C.
Notarás que los dos Pods pueden conectarse con éxito al servicio hello-server. Esto es porque aún no definiste una política de red para restringir el acceso. En cada una de estas ventanas, deberías ver respuestas exitosas por parte del servidor.
Tarea 5. Restringe el acceso mediante una política de red
Ahora bloquearás el acceso al Pod hello-server de todos los Pods que no tengan la etiqueta app=hello.
La definición de la política que usarás está incluida en el archivo manifests/network-policy.yaml.
- Aplica la política con el siguiente comando:
Resultado:
- Vuelve a mostrar las últimas líneas de los registros del cliente "bloqueado":
Ahora, en la ventana que muestra las líneas del cliente "bloqueado", verás que el resultado se ve así:
La política de red evitó la comunicación desde el Pod sin etiqueta a hello-server.
- Para salir, presiona Ctrl+C.
Tarea 6. Restringe los espacios de nombres con políticas de red
En el ejemplo anterior, definiste una política de red que restringe las conexiones en función de etiquetas de Pod. Por lo general, resulta útil etiquetar espacios de nombres completos, particularmente cuando los equipos o aplicaciones tienen sus propios espacios de nombres.
Modificarás la política de red para que solo permita el tráfico desde un espacio de nombres designado y, luego, moverás el Pod hello-allowed hacia ese espacio de nombres nuevo.
- Primero, borra la política de red existente:
Resultado:
- Crea la versión con espacio de nombres:
Resultado:
- Ahora observa los registros del Pod
hello-allowed-clienten el espacio de nombres predeterminado:
Notarás que ya no puedes conectarte a hello-server.
-
Para salir, presiona Ctrl+C.
-
Por último, implementa una segunda copia de la aplicación hello-clients en el espacio de nombres nuevo.
Resultado:
Prueba la tarea completada
Haz clic en Revisar mi progreso para verificar la tarea realizada. Si implementaste correctamente una segunda copia de la aplicación hello-clients en el espacio de nombres nuevo, verás una puntuación de evaluación.
Tarea 7. Validación
A continuación, revisa los registros de los dos clientes nuevos de hello-app.
- Ejecuta el siguiente comando para observar los registros de la aplicación con la etiqueta "hello" en el espacio de nombres
hello-appsde la aplicación:
Resultado:
Ambos clientes pueden conectarse con éxito porque, a partir de Kubernetes 1.10.x, las políticas de red no admiten la restricción del acceso a los Pods dentro de un espacio de nombres determinado. Puedes agregar a la lista de entidades permitidas etiquetas de Pods o de espacios de nombres, o la unión (es decir, OR) de ambas. Sin embargo, aún no puedes incluir en la lista la intersección (es decir, AND) de etiquetas de Pods y etiquetas de espacios de nombres.
- Para salir, presiona Ctrl+C.
Tarea 8. Eliminación
Qwiklabs se encargará de cerrar todos los recursos utilizados en este lab, pero esto es lo que debes hacer para limpiar tu propio entorno a fin de reducir los costos y ser un buen ciudadano de la nube:
- Sal del host de bastión:
- Ejecuta el siguiente comando para destruir el entorno:
Resultado:
Tarea 9. Soluciona problemas en tu propio entorno
Cuando se ejecuta Terraform, la secuencia de comandos de instalación falla y muestra el mensaje “Permission denied”
Las credenciales que usa Terraform no proporcionan los permisos necesarios para crear recursos en los proyectos seleccionados. Asegúrate de que la cuenta que se detalla en gcloud config list tenga los permisos necesarios para crear recursos. Si los tiene, vuelve a generar las credenciales predeterminadas de la aplicación mediante gcloud auth application-default login.
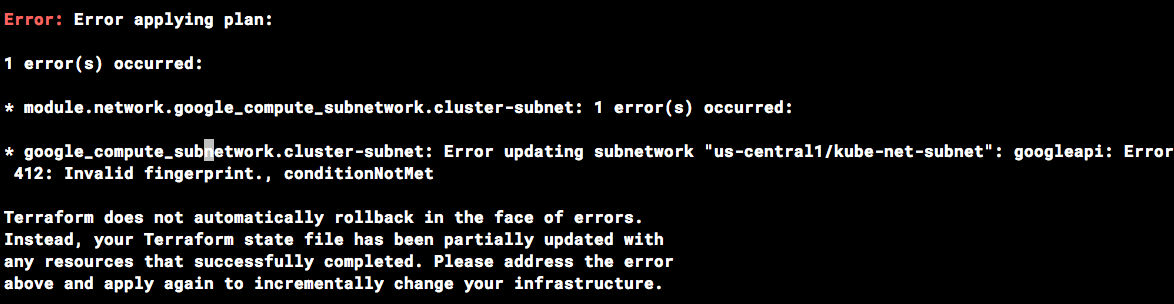
Error de huella digital no válida durante las operaciones de Terraform
En ocasiones, Terraform emite un mensaje de error de huella digital no válida al actualizar ciertos recursos.
Si ves el error que aparece a continuación, simplemente vuelve a ejecutar el comando.
¡Felicitaciones!
Aplicaste restricciones precisas a la comunicación de red para mejorar la seguridad de tu instancia de Kubernetes Engine.
Finaliza la Quest
Este lab de autoaprendizaje es parte de la Quest Google Kubernetes Engine Best Practices: Security. Una Quest es una serie de labs relacionados que forman una ruta de aprendizaje. Si completas esta Quest, obtendrás una insignia como reconocimiento por tu logro. Puedes hacer públicas tus insignias y agregar vínculos a ellas en tu currículum en línea o en tus cuentas de redes sociales. Inscríbete en esta Quest y obtén un crédito inmediato de realización. Consulta el catálogo de Google Cloud Skills Boost para ver todas las Quests disponibles.
Realiza tu próximo lab
Continúa tu Quest con Cómo endurecer las configuraciones de clústeres de GKE predeterminadas, o revisa otros labs de Google Cloud Skills Boost:
- Seguridad de Google Kubernetes Engine: Autorización binaria
- Cómo utilizar el control de acceso basado en roles en Kubernetes Engine
Próximos pasos/Más información
- Terraform Google Provider
- Políticas de red de Kubernetes
- Kubernetes Engine: Crea una política de red de clúster
- Kubernetes Engine: Instructivo sobre políticas de red
- Kubernetes Engine: Endurecimiento de la seguridad del clúster
Capacitación y certificación de Google Cloud
Recibe la formación que necesitas para aprovechar al máximo las tecnologías de Google Cloud. Nuestras clases incluyen habilidades técnicas y recomendaciones para ayudarte a avanzar rápidamente y a seguir aprendiendo. Para que puedas realizar nuestros cursos cuando más te convenga, ofrecemos distintos tipos de capacitación de nivel básico a avanzado: a pedido, presenciales y virtuales. Las certificaciones te ayudan a validar y demostrar tus habilidades y tu conocimiento técnico respecto a las tecnologías de Google Cloud.
Última actualización del manual: 18 de octubre de 2023
Prueba más reciente del lab: 18 de octubre de 2023
Copyright 2024 Google LLC. Este software se proporciona tal como está, sin garantías ni declaraciones para ningún uso o propósito. El uso que hagas de él está sujeto a tu acuerdo con Google.